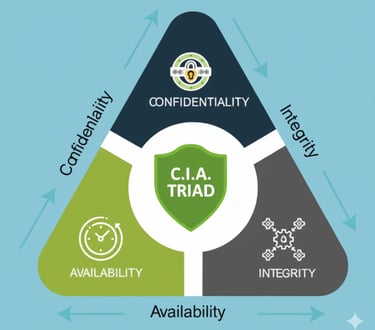
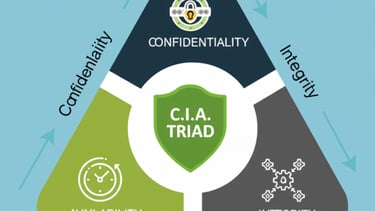
CIA Triad–Driven Security Approach
Our security assessments are built around the CIA Triad — Confidentiality, Integrity, and Availability. Every identified vulnerability is evaluated based on how it affects:
Confidentiality: Protection of sensitive data from unauthorized access
Integrity: Assurance that data and systems are accurate and unaltered
Availability: Ensuring systems and services remain accessible when needed
This ensures a balanced and industry-aligned security evaluation.
Each vulnerability is ranked based on impact and likelihood, with explicit reference to its effect on the CIA Triad. This allows stakeholders to clearly understand business and technical risk.





We follow recognized security standards and best practices to ensure thorough, reliable results. Our methodology aligns with real-world attack scenarios and defensive controls.
Clear Risk Severity Classification
Evidence-Based Proof of Findings






We bring proven experience and deep technical knowledge to every project. Our team follows industry best practices and recognized standards to ensure reliable, high-quality results.
Expertise You Can Trust
Professional, Confidential Reporting
Our reports are structured for both technical and non-technical audiences while maintaining strict confidentiality and data protection throughout the engagement.
Beyond identifying risks, we offer clear, practical remediation steps that help restore and strengthen confidentiality, integrity, and availability across your systems.
Actionable & Practical Remediation
Expert & Standards-Based Assessments
We provide detailed proof for every finding, including testing steps, observations, and validation evidence, ensuring transparency and credibility.
Our Work
Real results from tailored cybersecurity solutions.


Network Shield
Secured a multinational’s network against persistent threats.






Cloud Guard
Protected cloud infrastructure for a fast-growing startup.
Zeroday’s team swiftly identified vulnerabilities in our network, giving us peace of mind with their thorough and professional approach.
Ashish Kumar
CEO AD DIGITAL ONE


★★★★★
